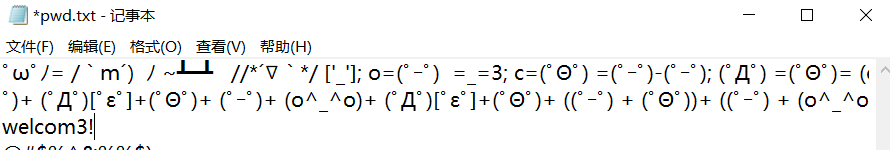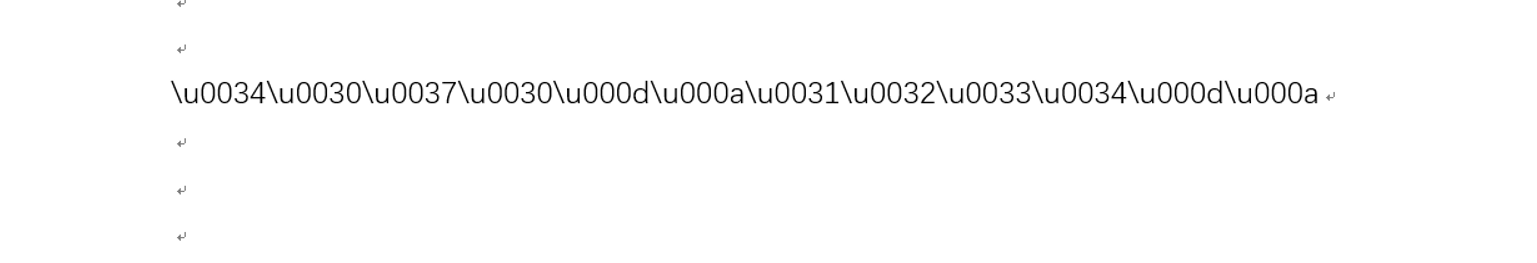[GKCTF 2021]签到 签到题 x 猜flag √
这是一道靠猜的题目
image-20210727211853547
发现一些小细节
http追踪流
image-20210727211937583
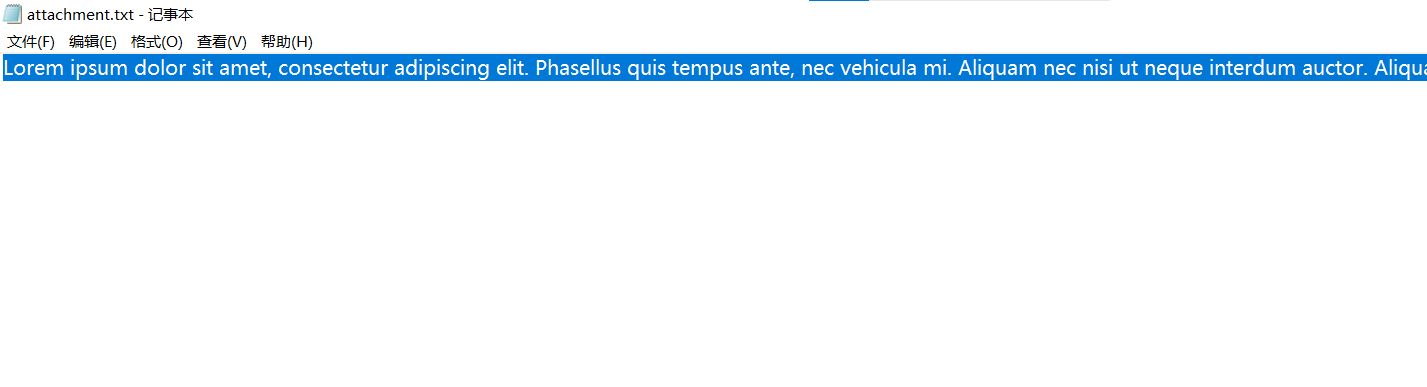
数字蛮奇怪的,往下翻image-20210727212449419
base64,那就是16进制转文本再转base64
转完我直接沉默
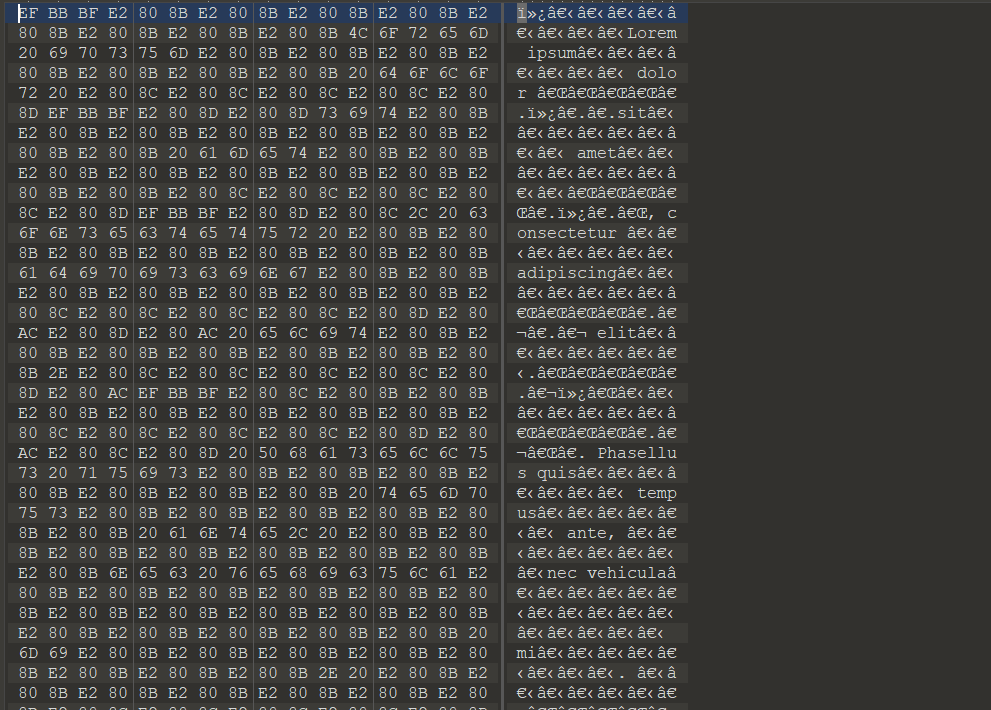
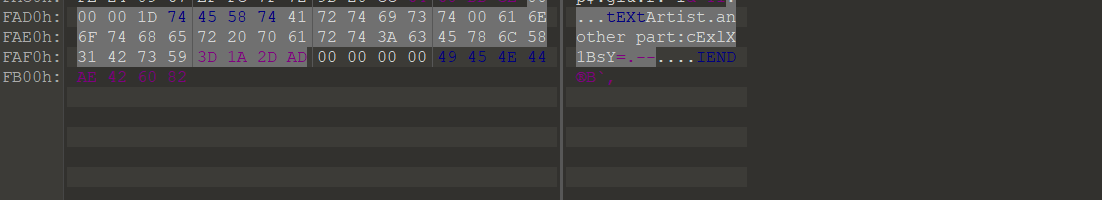
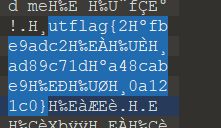
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 44516 f4e4367306a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d4b44534d674943416749434167494341344d446f784d446f774d6941774d79307a4d4330784d6a417949434167494341674943416749776f4e49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a49794d6a436730744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c5330744c516f3d80 :10 :02 03 -30 -1202 #
1 2 3 4 5 6 7 8 9 10 11 12 13 14 64306c455357644251306c6e51554e4a5a3046355355737764306c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154576c44546d39525241707154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7162314645616b46445357644251306c6e51554e4a5a32644554545a46524530325157704e5a3046365458524e524531305257704e436e5177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d644442705130354e65556c7154586c4a616b31355357704e65556b4b4e6b467154576442656b31305455524e644556715458644a616b38775a566f324d6d56774e557377643074795556645a64315a485a48593152556c3051576c4e4d5546355a4777316255733254545a7162475a7763573579555552304d464e4d64444254544170304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d537a42425357526159585a764e7a567462485a735130354e564530325255524e436e6f77655531334d464e4e6555467154545a524e327877596a647362584a5252484a7a5131706f516c68614d446c745647637751306c355655524a4d315a74596e4676656d3951567974736357563151303477553078304d464e4d64444254544851775530774b63336858576d786b4d5659354d544e6c4e325179576d684752324a7a576d31615a7a427363446c7064573569567974585a7a427363446c7064573569567974585a7a427363446c706457356956797458537a423354586876564531336230524e6555464454517045546a4252524534775555527356324636546c684e65444258596d593562464a48556b524f5245347759584a6b4d464a6d4f565a6162444658596e644252456c6b556d46746345524c61577832526b6c6b556d46746345524c61577832566b747754544a5a436a303955556c6f545442525245347755516f3d
仔细观察你会发现这两段的相似之处
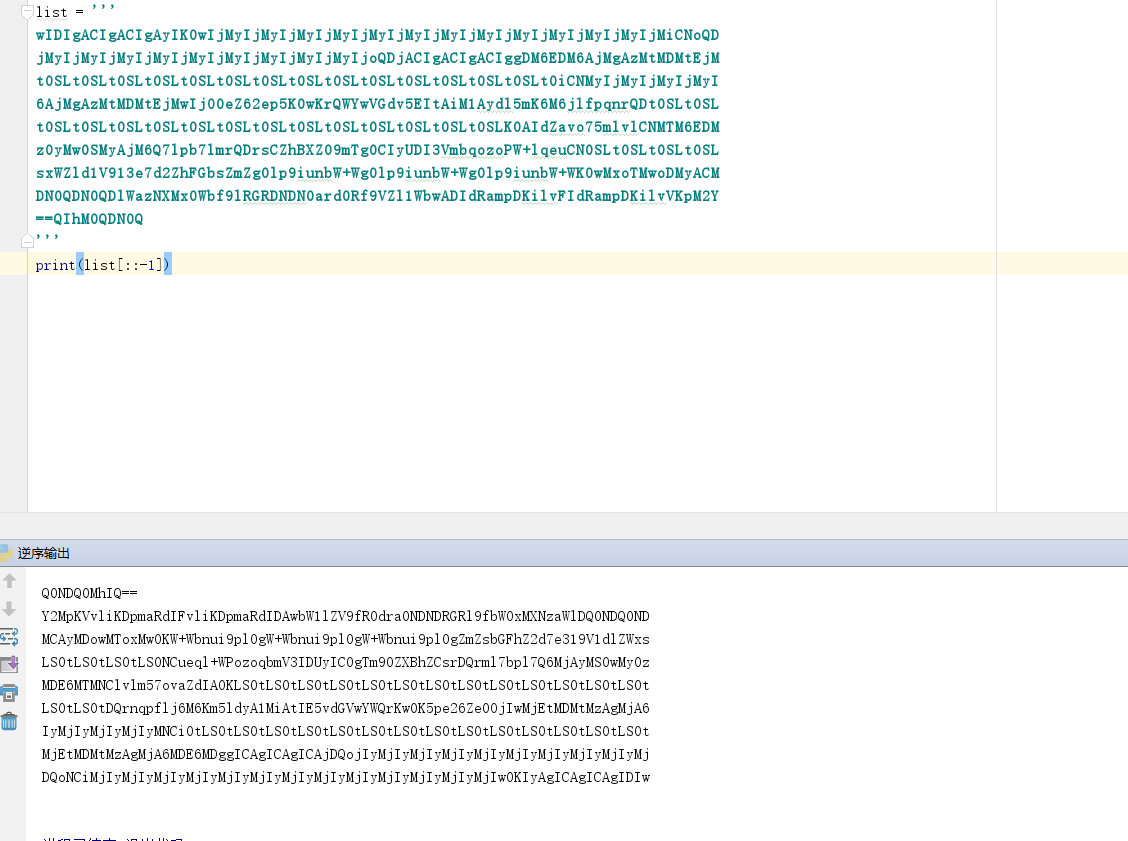
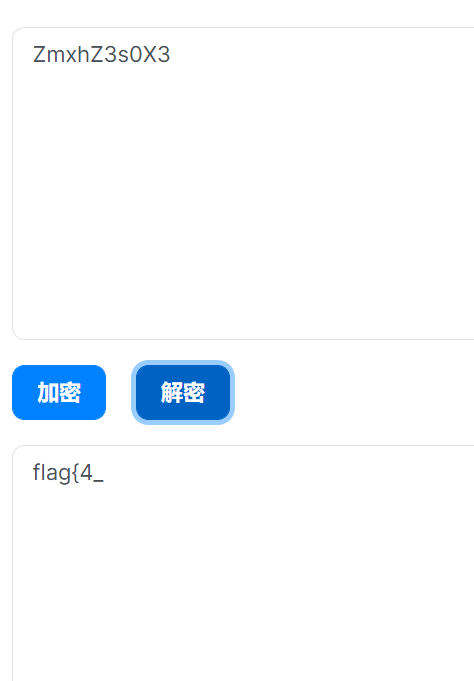
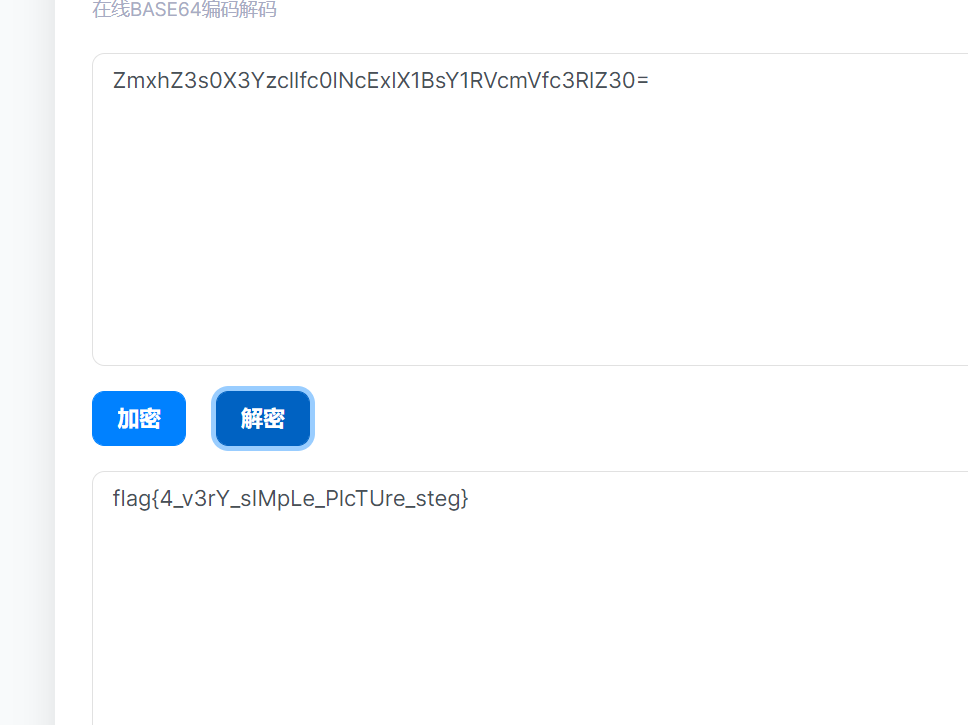
最后那串base64是反着的,那就
image-20210728232146423
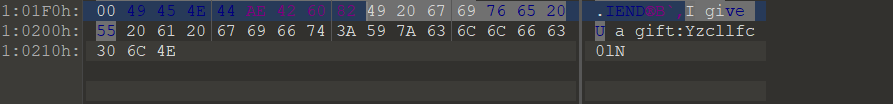
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 Q0NDQ0MhIQ==00 mmee__GGkkCC44FF__mm11ssiiCCCCCCC0 20 :01 :13 52 - Notepad++2021 -03 -301 :13 52 - Notepad++2021 -03 -30 20 :###########-21 -03 -30 20 :01 :08 #20
你猜猜flag是什么,反正我没猜到
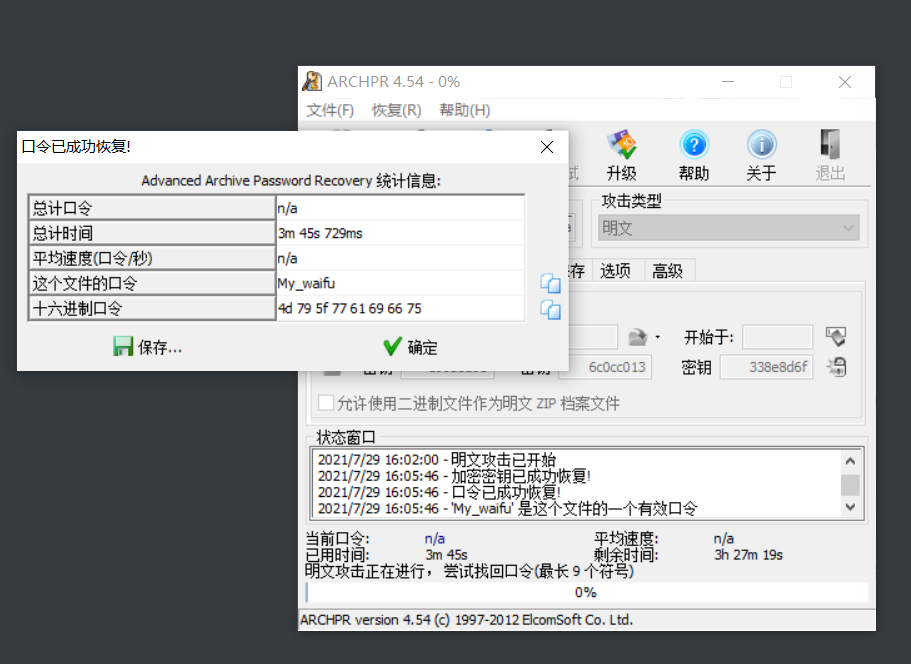
1 flag {Welc0 me_GkC4 F_m1 siCCCCCC!}
绝了
hashcat image-20210728233320953
无后缀文件,看了一下应该是某个办公软件的文件
随便改一个,
image-20210728233715495
手动爆破是不可能的,上网搜一下工具 Accent OFFICE Password Recovery破解版
image-20210729001711425
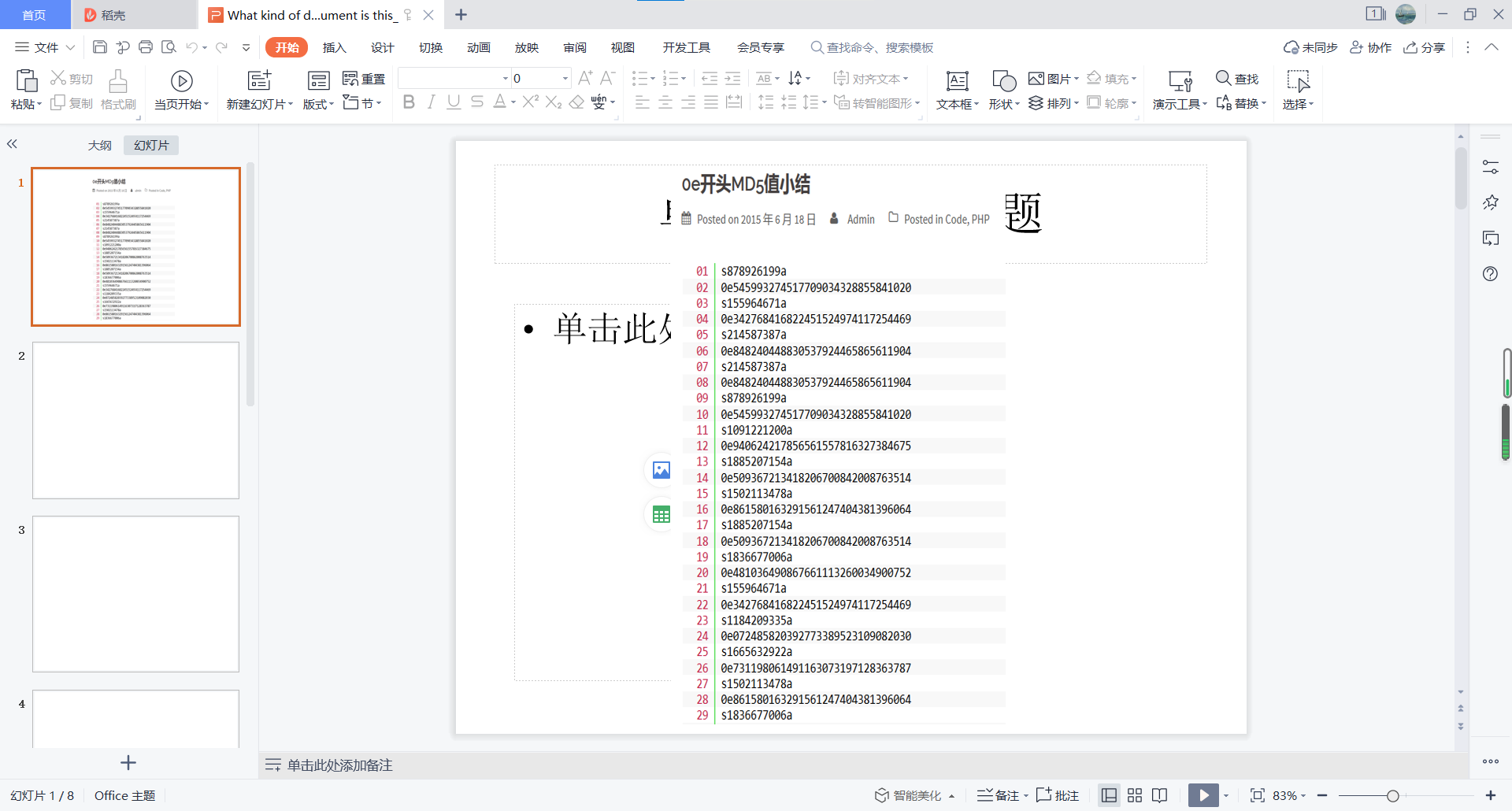
docx打开是乱码,试一下ppt
image-20210729001844141
有点东西
image-20210729002025008
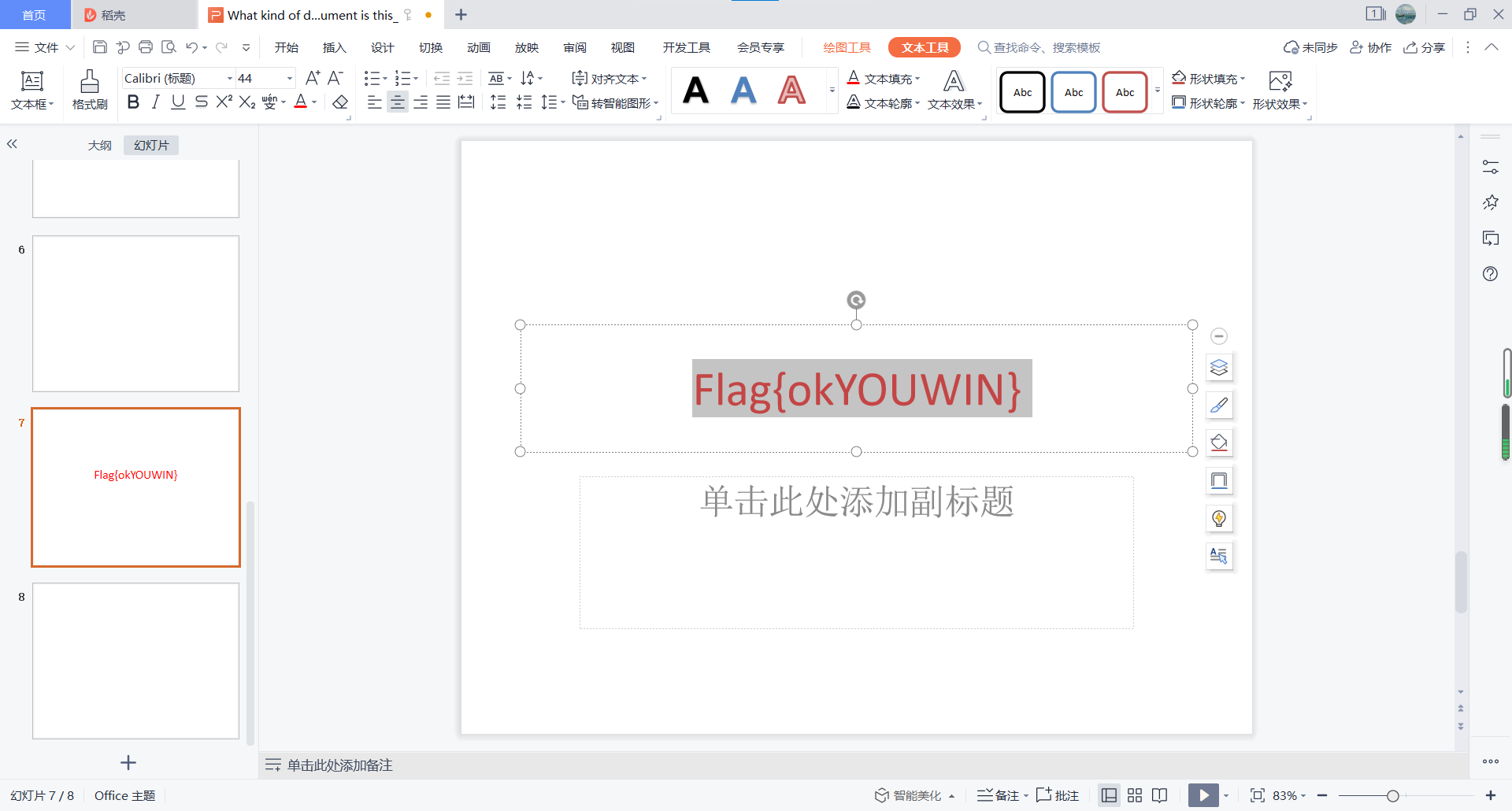
第七页ppt有惊喜。
[UTCTF2020]zero image-20210729112610362
有一种英文夹带法语的感觉(我看不懂我开始乱说
image-20210729113027631
不太对劲,查了一下这里是零宽度字符隐写:https://330k.github.io/misc_tools/unicode_steganography.html
image-20210729112513636
[SCTF2019]电单车 音频只响了一声,像是锁车的声音,沿着题目搜到了题目描述
1 2 题目描述:截获了一台电动车的钥匙发出的锁车信号,3 分钟之内,我要获得它地址位的全部信息。flag内容二进制表示即可。
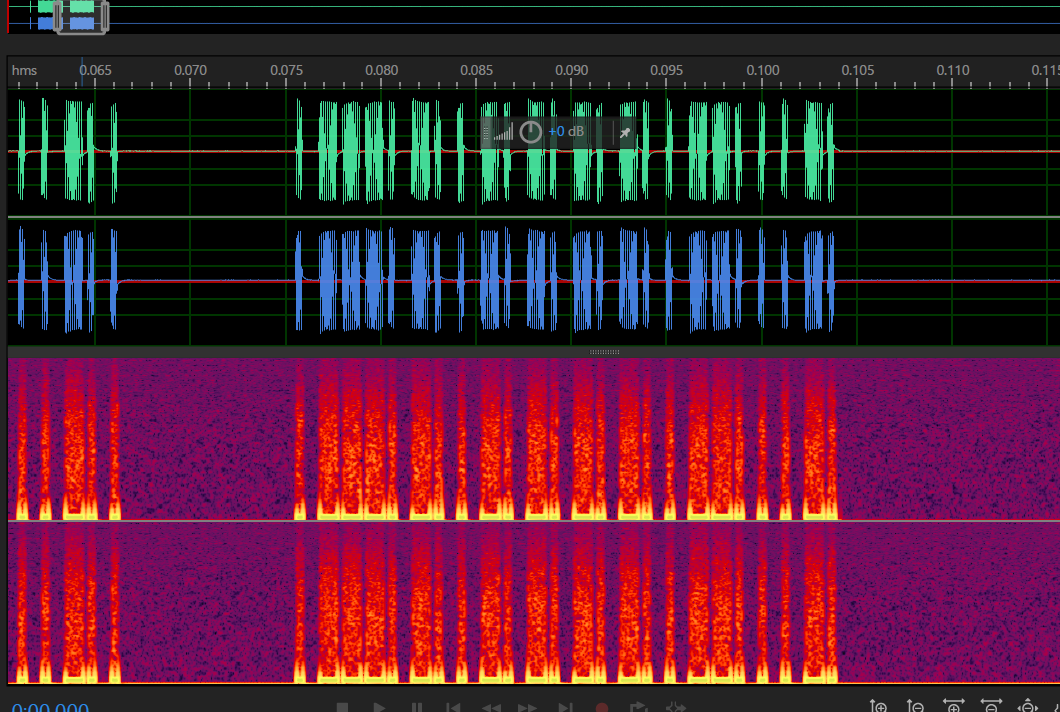
二进制啊,这就找高低频
image-20210729122824094
image-20210729122837549
这里分成了三段
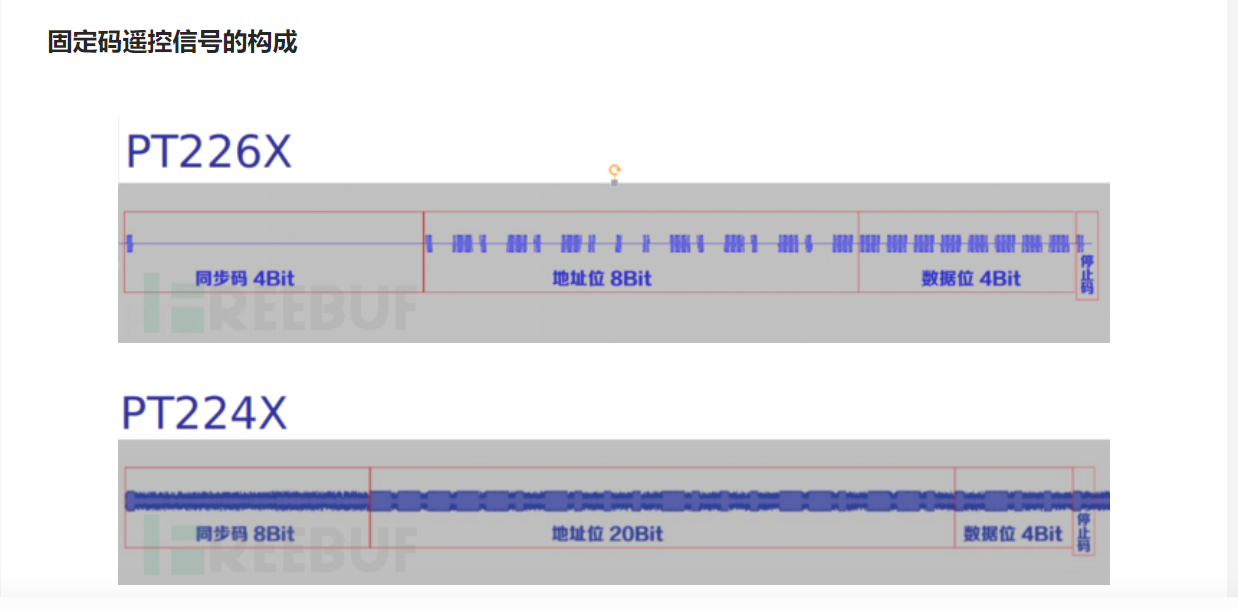
关于固定码 https://www.freebuf.com/articles/wireless/191534.html
image-20210729123137550
所以只要把第二段的二进制整理出来就行
[*CTF2019]otaku 第一层伪加密第二层明文爆破
image-20210729160327466
lastword?应该是明文了
在doc文件找找看
image-20210729160307504
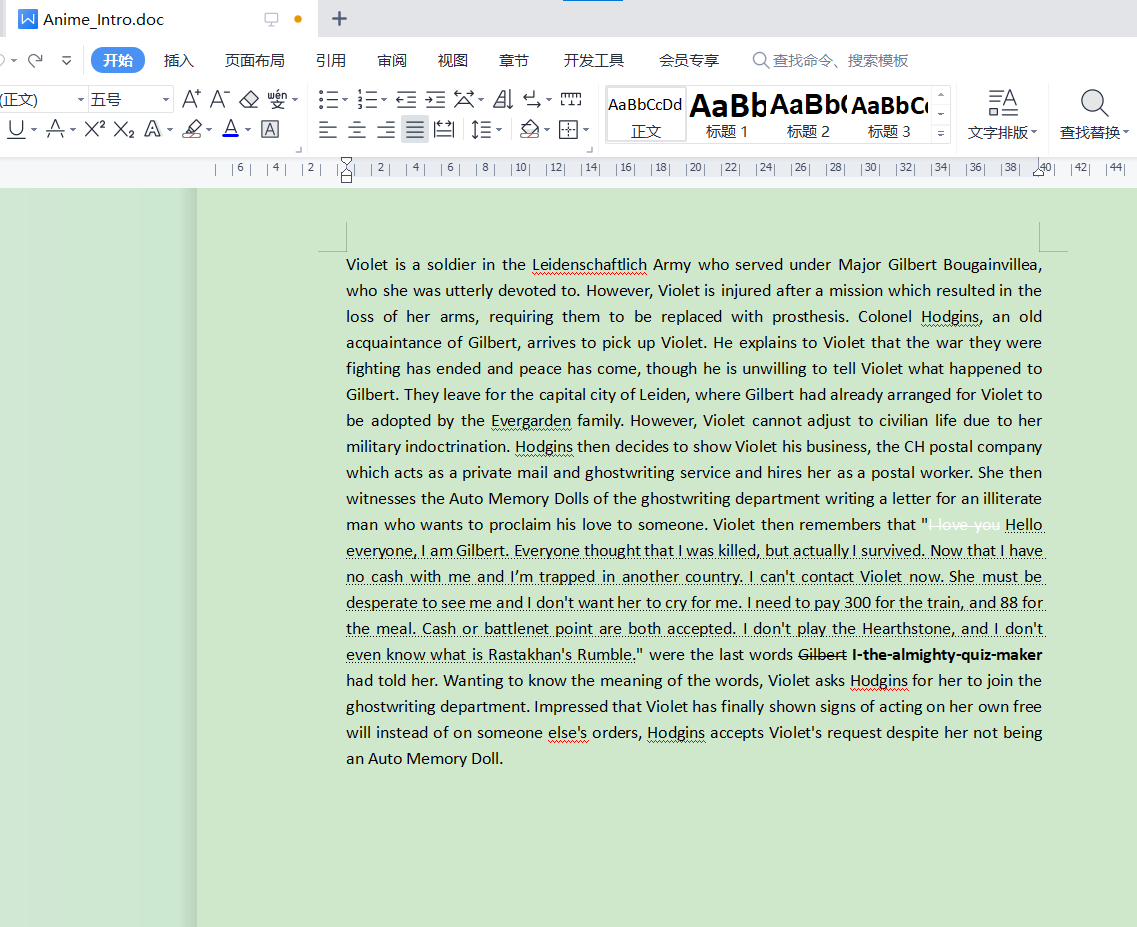
我看到的长这样,护眼和显示隐藏文字都开了这波着实被坑,就没摸到重点,把各种有标注的文字都尝试作为明文破解的文件发现都不对,上网搜到提示gbk编码隐藏文字部分
1 2 3 4 5 6 "1.txt" , "w" )"Hello everyone, I am Gilbert. Everyone thought that I was killed, but actually I survived. Now that I have no cash with me and I’m trapped in another country. I can't contact Violet now. She must be desperate to see me and I don't want her to cry for me. I need to pay 300 for the train, and 88 for the meal. Cash or battlenet point are both accepted. I don't play the Hearthstone, and I don't even know what is Rastakhan's Rumble."
image-20210729160736090
就可以愉快的爆破了
image-20210729161535289
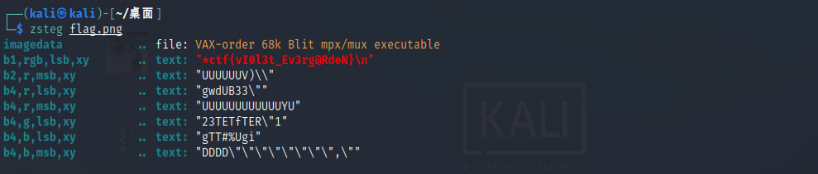
zsteg可以直接分离出flag
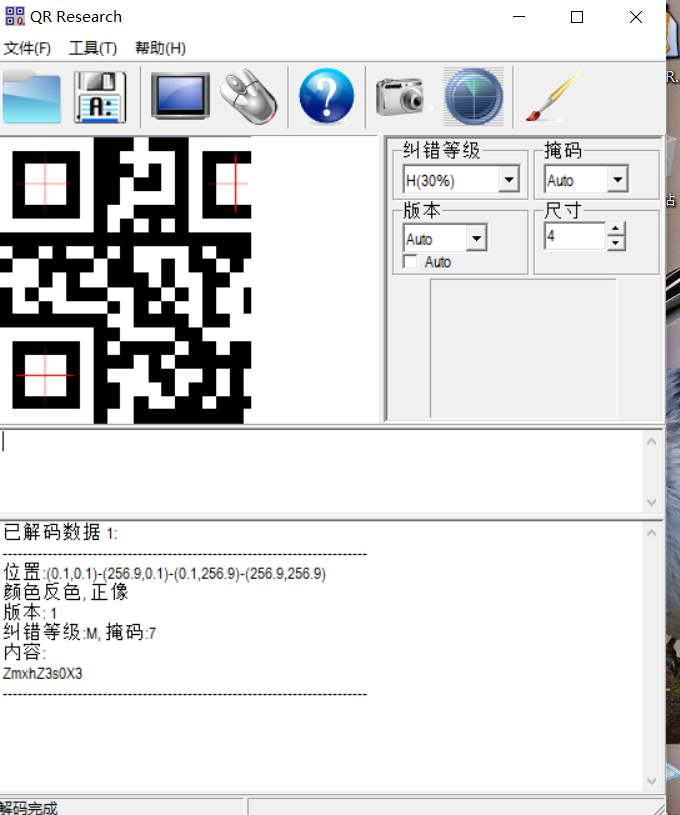
[湖南省赛2019]Findme 这题比我想象的离谱多了
1.png image-20210729163607327
感觉信息量很大但是没什么线索
image-20210729163927298
但是这图绝对有问题,先放一放
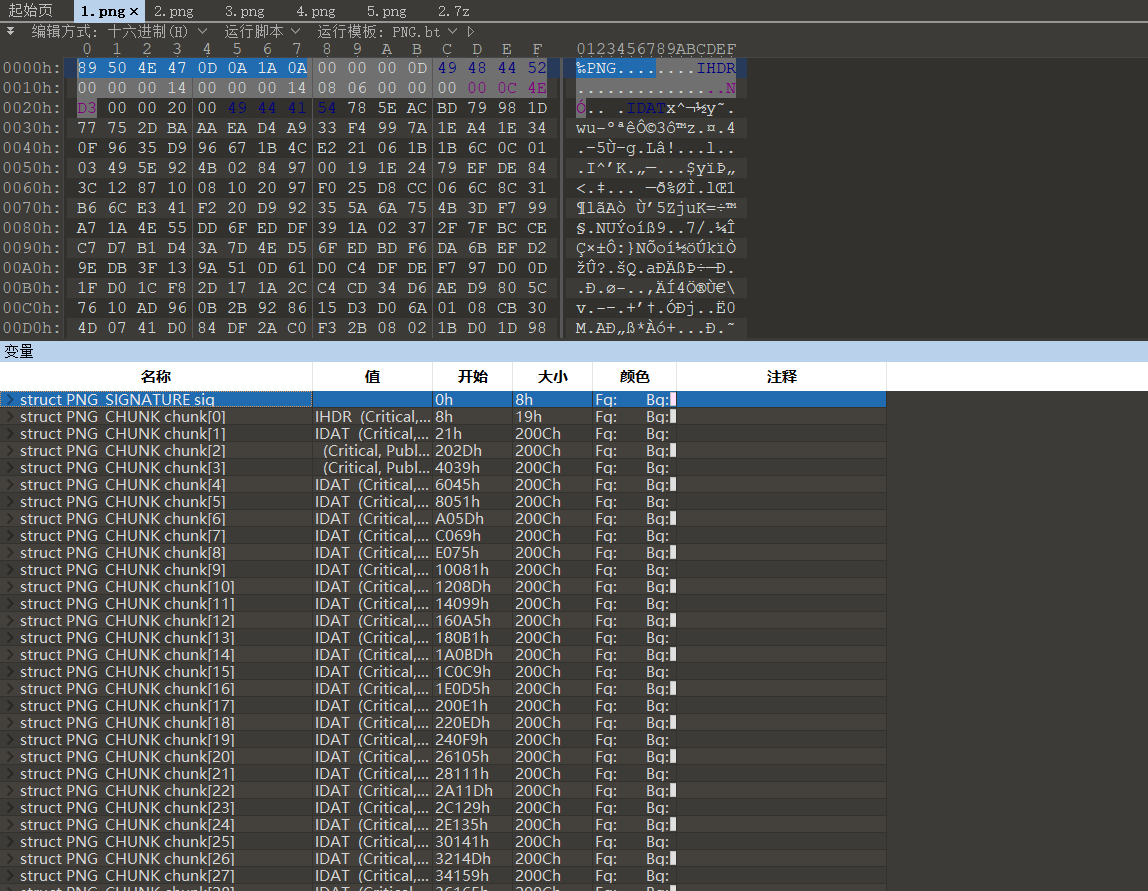
四张图折腾完再来看这个大量的IDAT应该有点问题
与其他四张图对比,宽高应该是要修改的
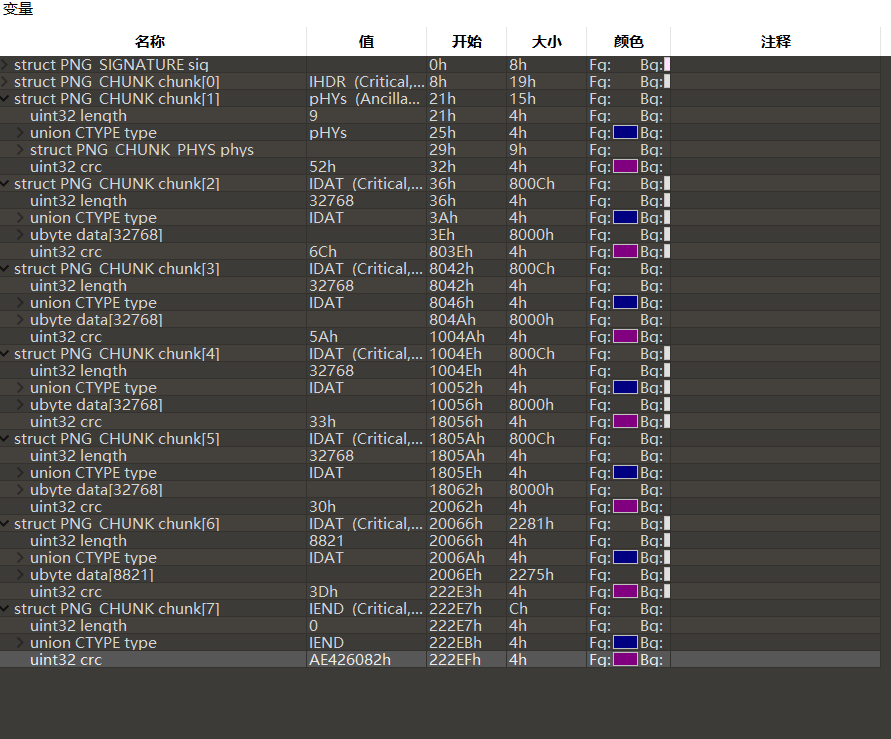
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 import zlibimport struct'1.png' 'rb' ).read()12 :29 ])0xC4ED3 4095 for w in range(n): '>i' , w))for h in range(n): '>i' , h)) for x in range(4 ): 4 ] = width[x] 8 ] = height[x] if crc32result == crc32key: for x in range(4 ): 16 ] = width[x]20 ] = height[x] '.png' ,'wb' ) ''' 参数 如果 source 为整数,则返回一个长度为 source 的初始化数组; 如果 source 为字符串,则按照指定的 encoding 将字符串转换为字节序列; 如果 source 为可迭代类型,则元素必须为[0 ,255] 中的整数; 如果 source 为与 buffer 接口一致的对象,则此对象也可以被用于初始化 bytearray。 如果没有输入任何参数,默认就是初始化数组为0个元素。 '''
然后修改
image-20210729172259582
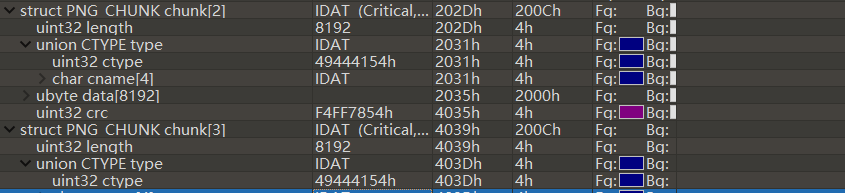
chunk[2]和[3]的uint32 type 令其十六进制数为49444154h
image-20210729172417096
没有比较就没有伤害。。。。。。。
image-20210729172523975
有点东西
image-20210729175010276
那就把五段拼起来,看起来不是图片顺序
2.png 文件尾藏了一个疑似7z压缩的压缩包实则是zip压缩,需要将所有的7z改成PK
image-20210729164716150
找大小不一样的
image-20210729164744709
3.png crc报错,尝试修改其图片高不是很成功
仔细观察各个IDAT的crc和IEND的crc对比
image-20210729165528558
提取出来看看
image-20210729165803797
4.png image-20210729165939840
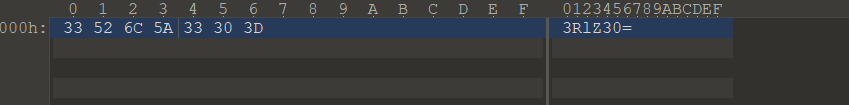
这边的=和.-为干扰
5.png image-20210729170340714
找到开头
image-20210729175411089
1-5-4-2-3
image-20210729175645466
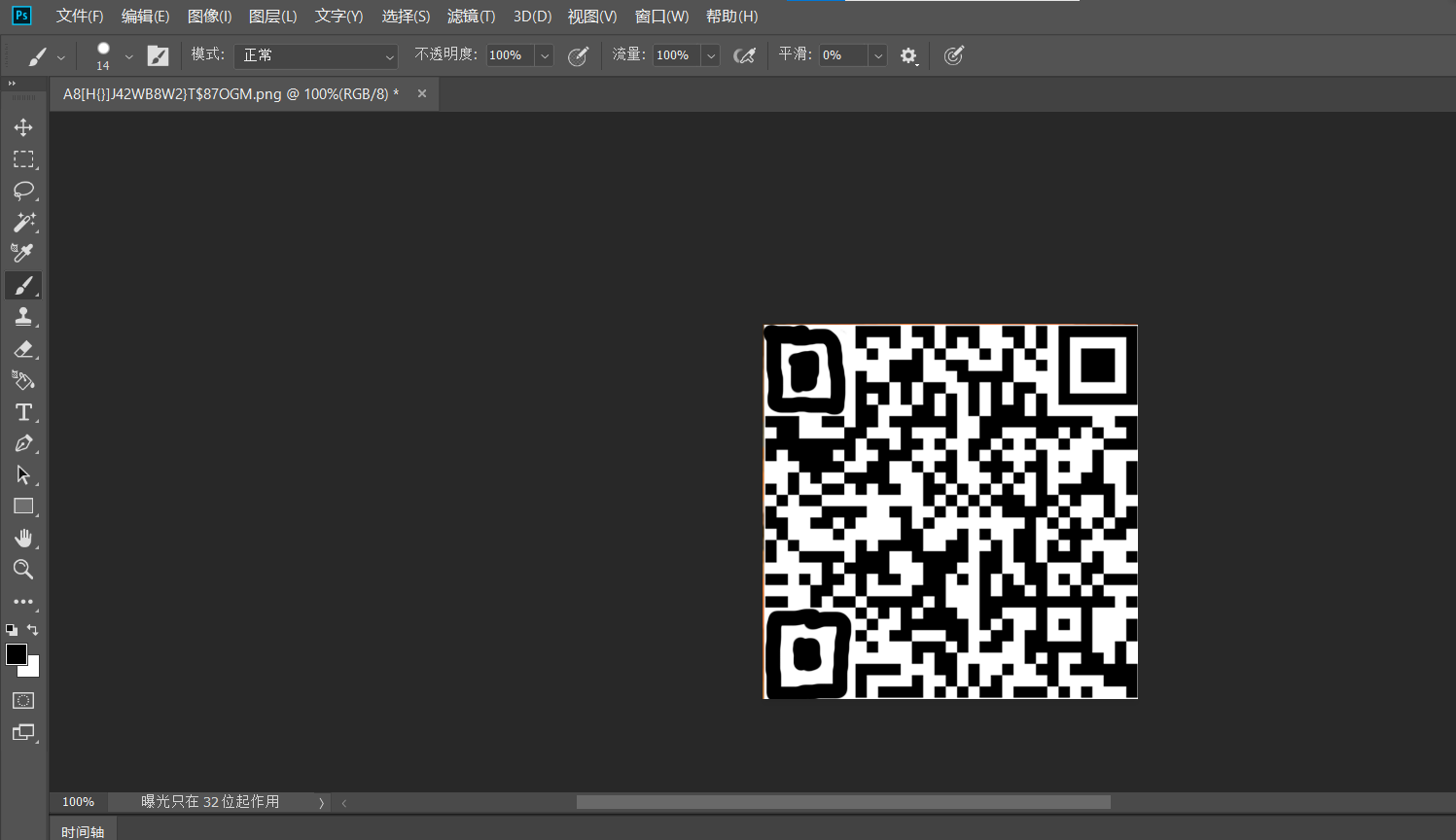
[QCTF2018]X-man-A face 补齐二维码就行,手机扫一扫
image-20210729191035177
(别问,问就是徒手补二维码)然后base32
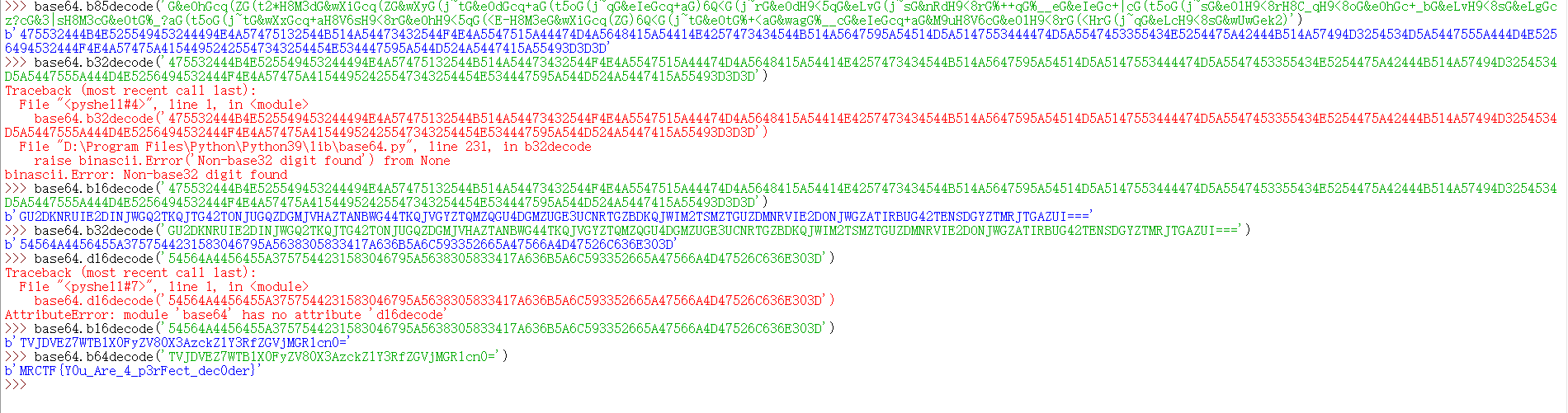
[MRCTF2020]pyFlag 三张图片尾有惊喜,可以拼成一个zip压缩包,爆破得密码为1234,然后真base套娃现场
image-20210729193557484
真的很杂 图片套apk(我之前以为是压缩包,尬住了,后缀直接改成apk,在手机上安装
我以为出flag了,(我还是太年轻了
image-20210729203831755
image-20210729203847098
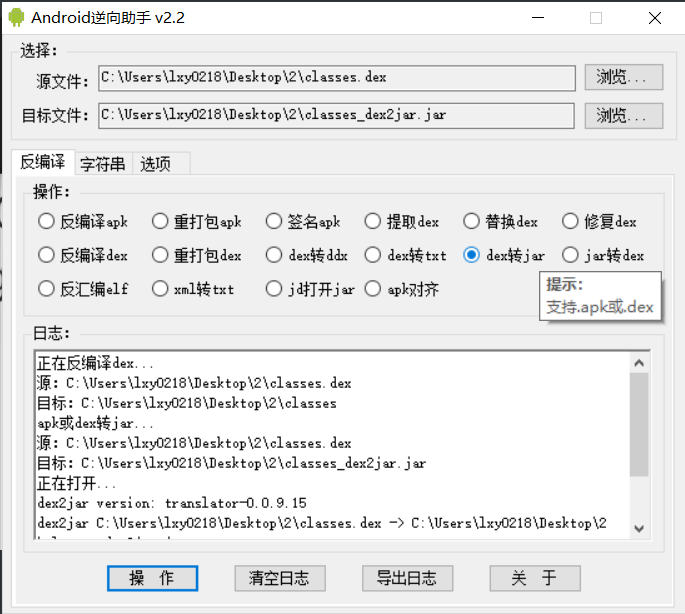
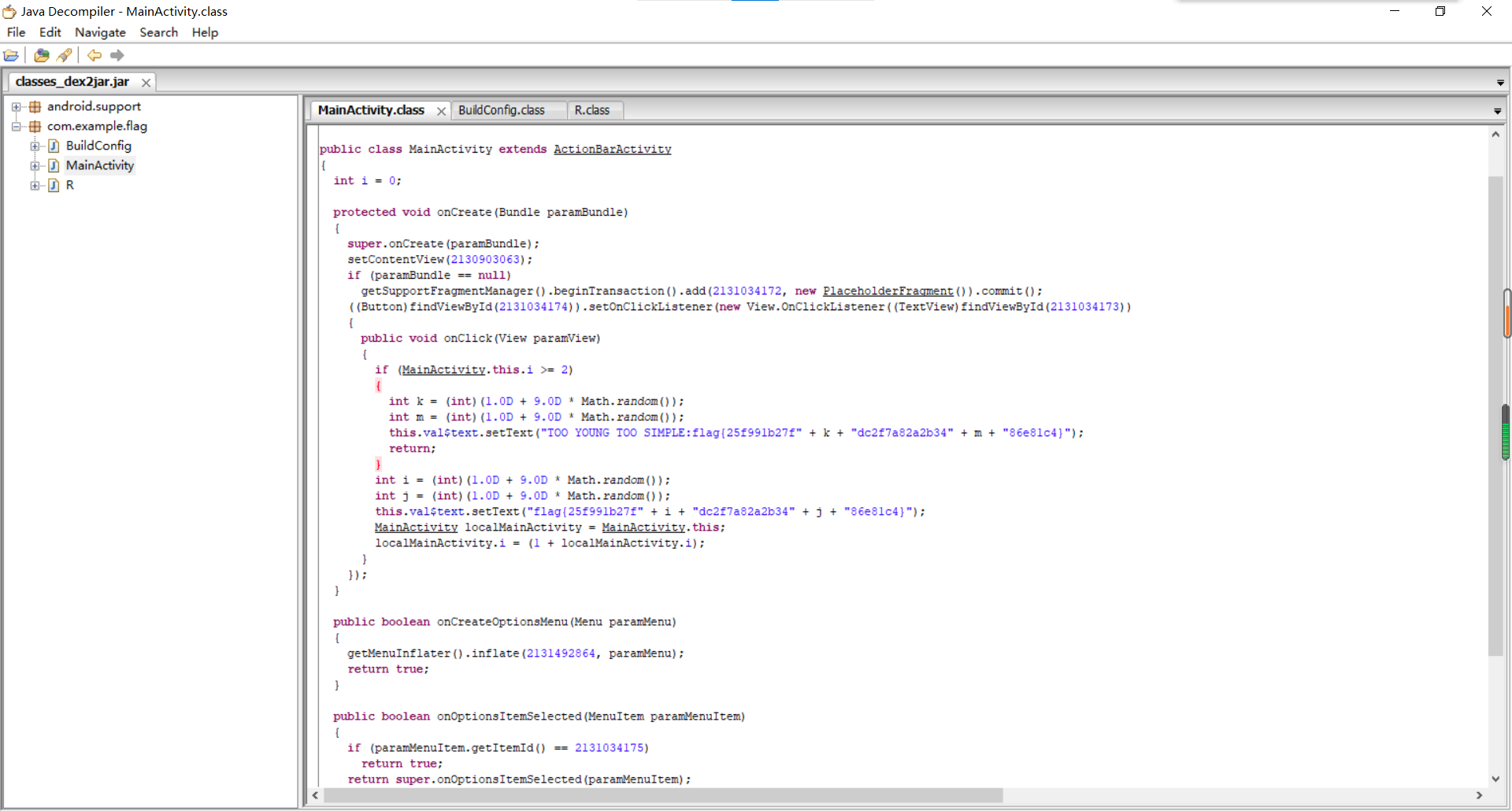
转成java
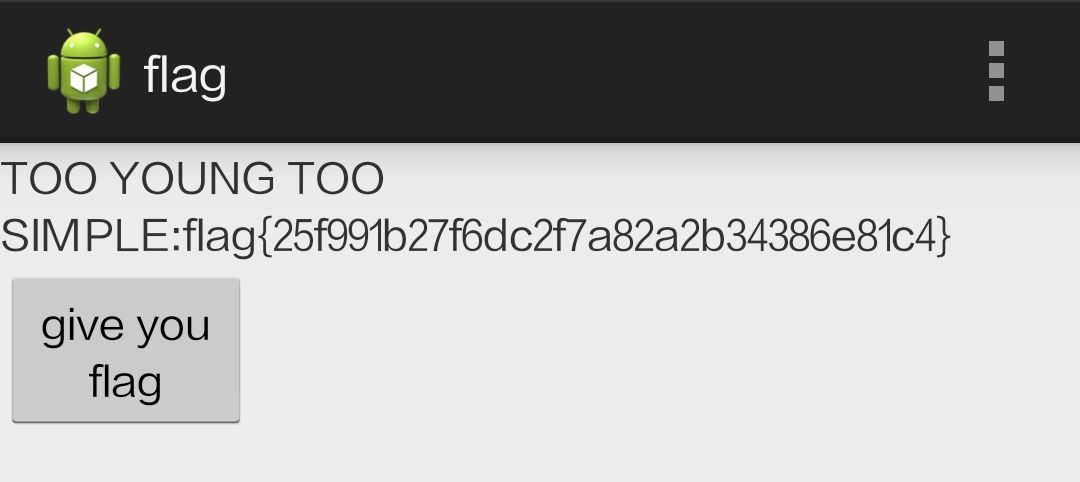
image-20210729203922006
有两位数是随机出的。。。。。。。。猜吧
1 flag {25 f991 b27 fcdc2 f7 a82 a2 b34386 e81 c4 }
Business Planning Group png套bpg,用honeyview即可打开bpg文件
image-20210729210450928
base64,结束 {BPG_i5_b3tt3r_7h4n_JPG}bpg是另一种jpg,hhh
[watevrCTF 2019]Evil Cuteness 把图片藏的压缩包打开就行
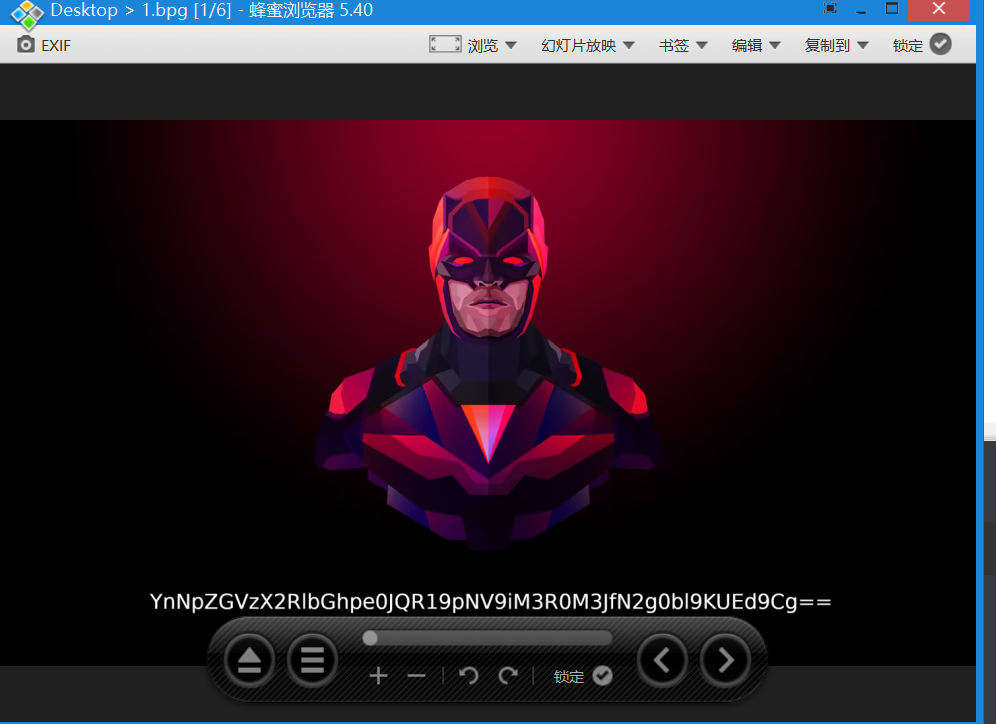
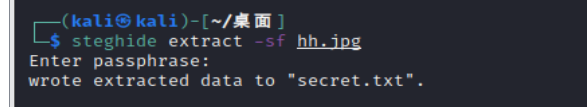
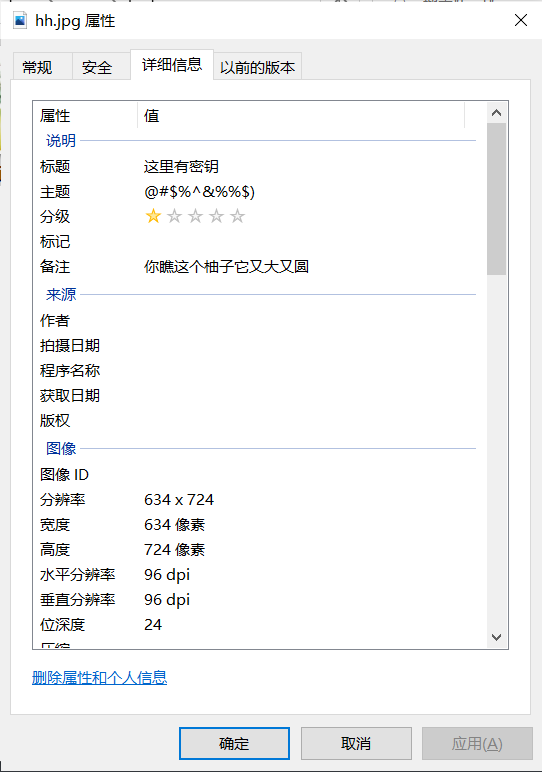
[ACTF新生赛2020]剑龙 hh.png为steghide隐写密码为pwd.txt的颜文字解密后的结果
image-20210729232451785
image-20210729232509358
image-20210729232550478
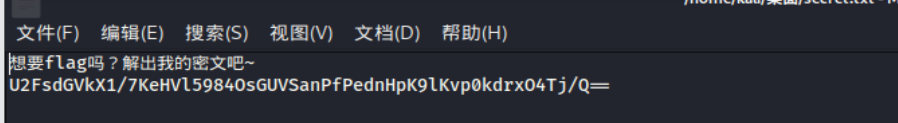
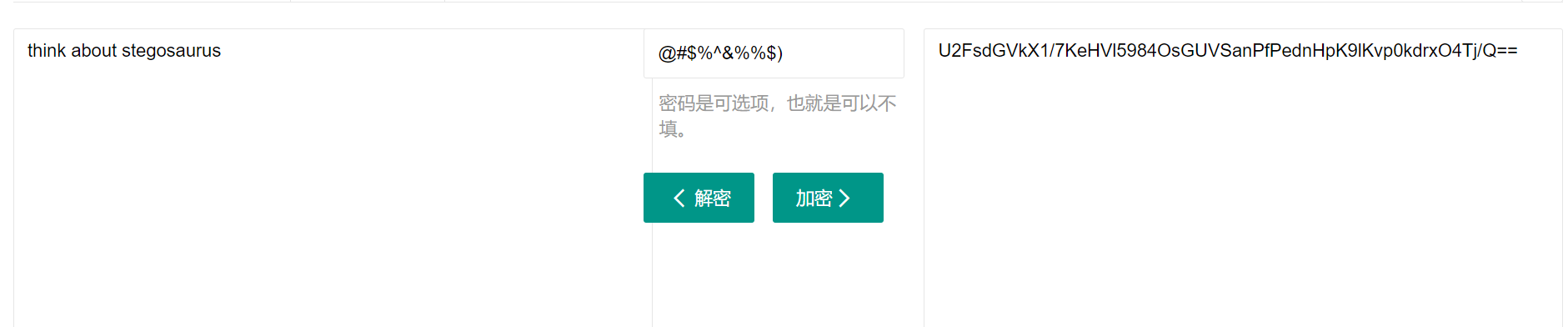
密钥在哪里
image-20210729232618705
image-20210729232843136
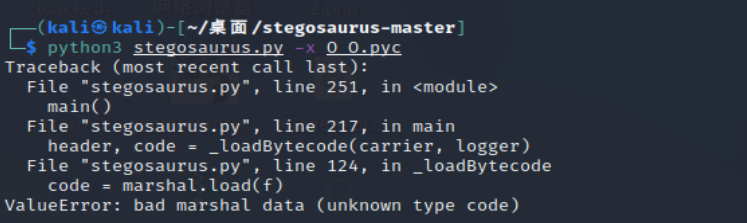
stegosarus?搜一下好了,剑龙加密,只有对pyc pyo py文件才有用的
作为一个成功的翻车选手
image-20210730221850899
这合理吗,这真实吗
voip 是个流量包,看了好久啥都没发现,只有udp流
搜了才知道voip是VoIP,对voip:互联网协议语音(VoIP),也称为IP电话,简称电话。 将其放在wireshark中,选择电话,voip呼叫。
就可以听到flag了,是英文(听力废物听了好多遍
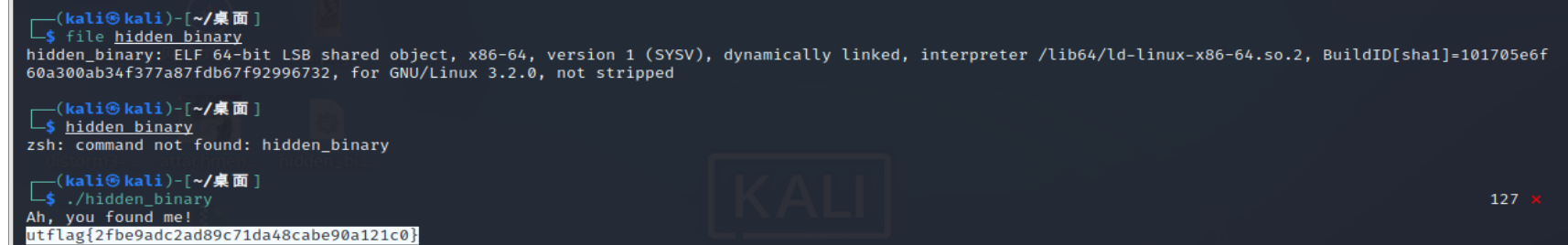
[UTCTF2020]File Carving 图片藏压缩包,压缩包里是ELF文件,直接在linux上运行就行,直接尝试直接搜索flag但是
image-20210729222923654
image-20210729223106550
[GUET-CTF2019]soul sipse 这个题目有点意思
image-20210729224043092
打开音频,鸡皮疙瘩都起来了,这个频率,感觉没有什么特点(像个杂音,听着头大
image-20210729225528565
有点东西,看起来是考隐写了
image-20210729225612031
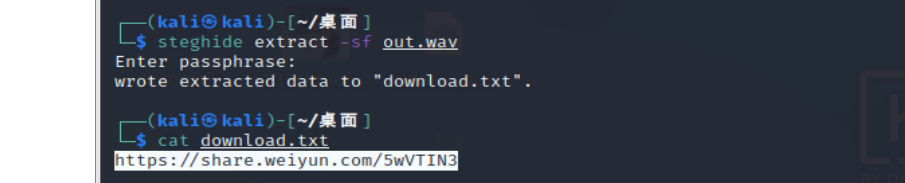
steghide无密码隐写,然后藏了一个微云链接,是png图片
image-20210729225722131
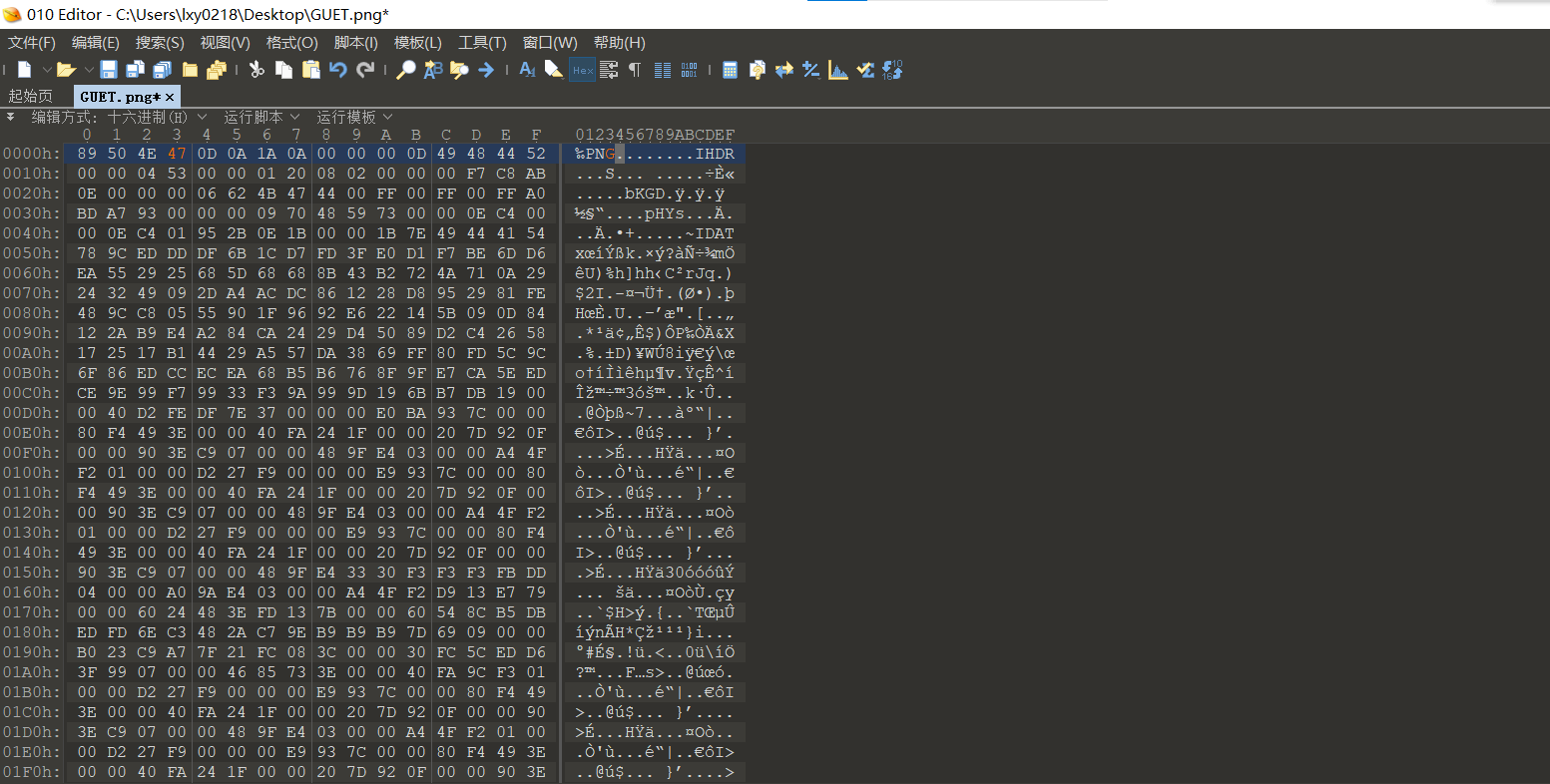
修改错误的文件头
image-20210729225809445
unicode
image-20210729230219993
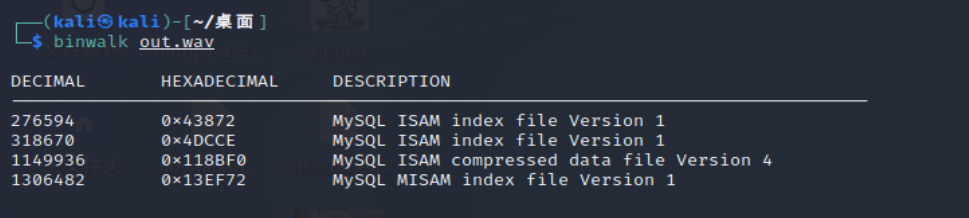
好像没提示了,看看音频吧
image-20210729230520431
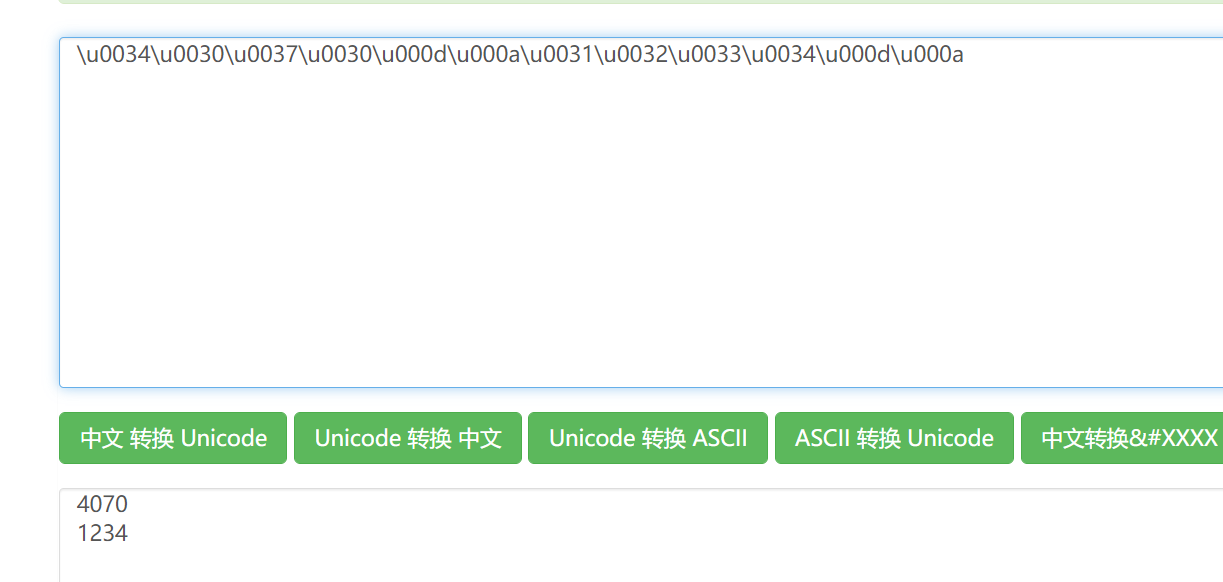
好家伙,这里藏了个hint,求和
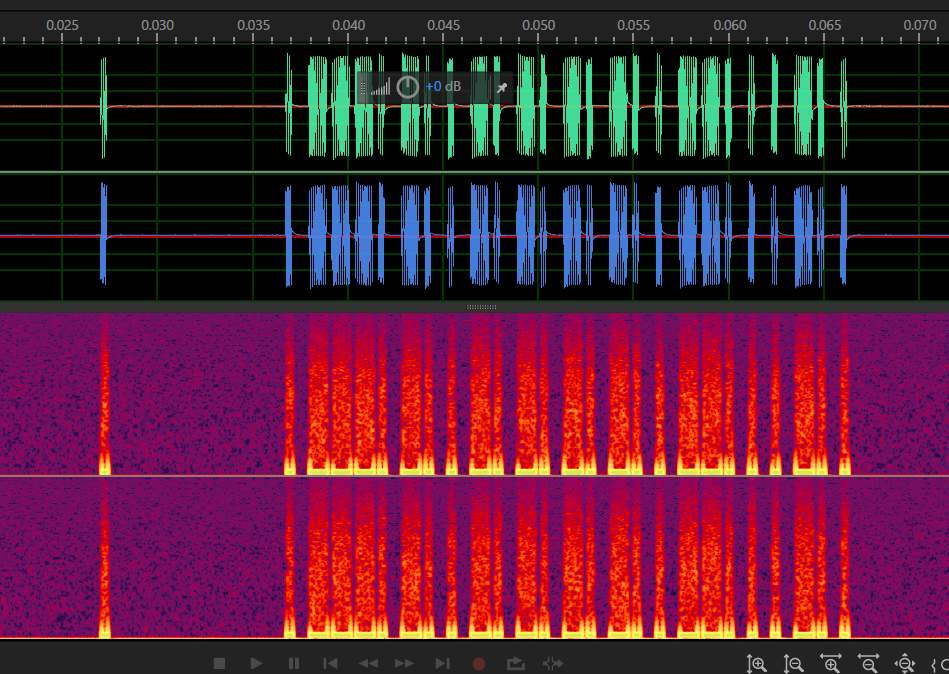
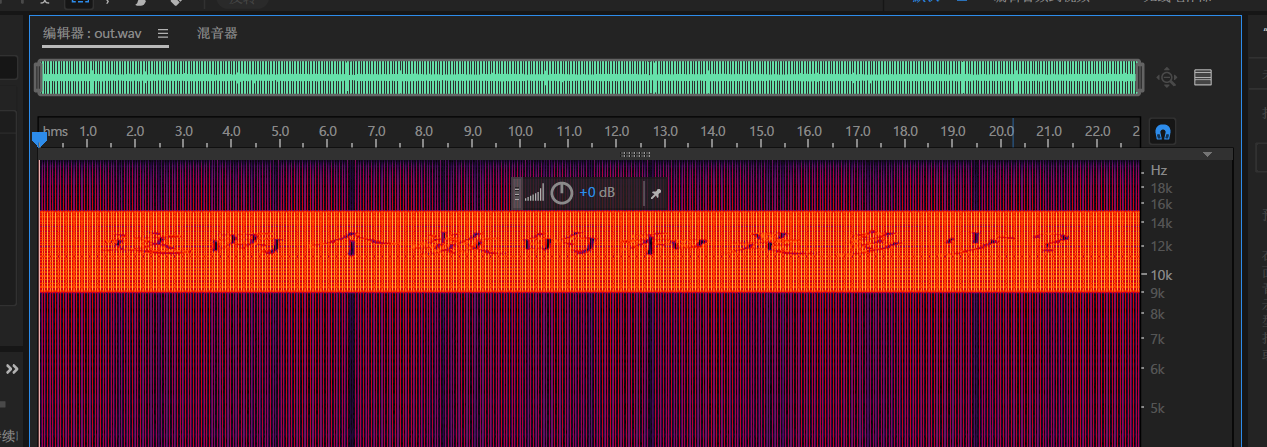
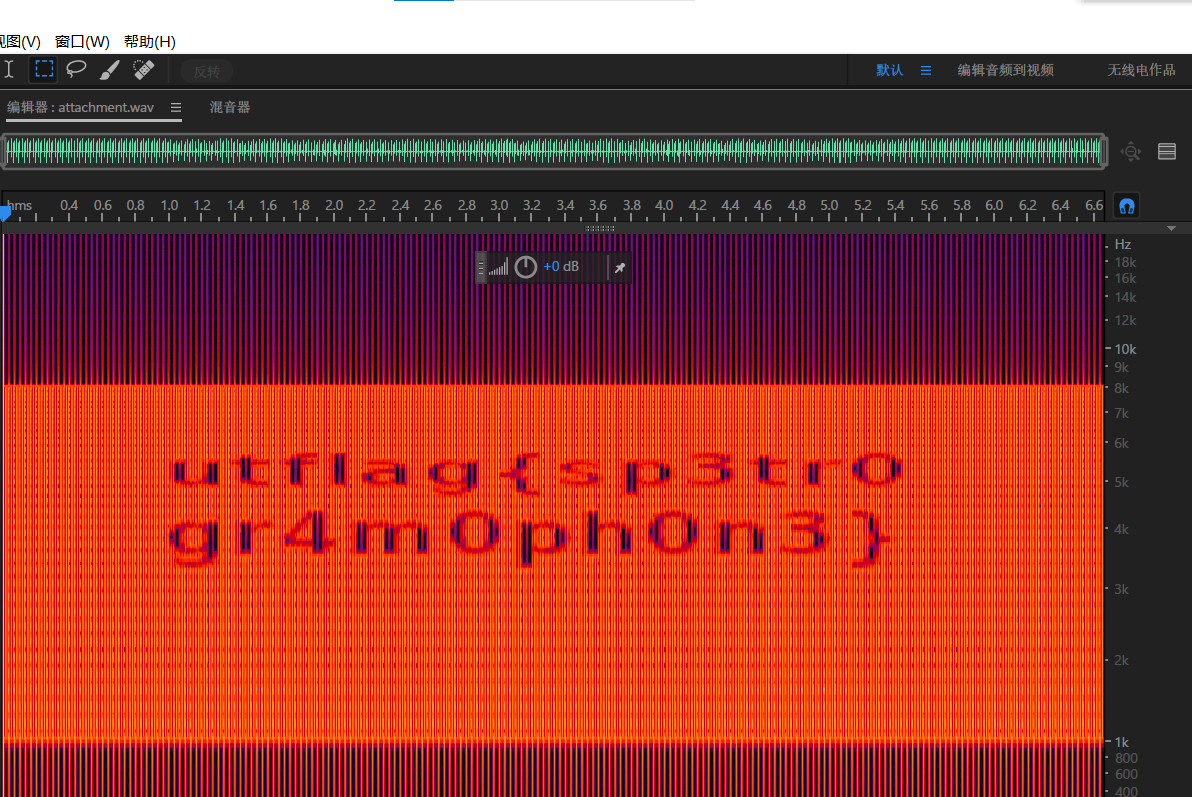
[UTCTF2020]spectogram 频谱隐写
image-20210729230646524